With the release of PowerShell 2.0, we now have a PowerShell module that we can use to administer Active Directory. The Active Directory Module for Windows PowerShell runs on Windows Server 2008 R2 and on Windows 7 and relies on a web service that is hosted on one or more domain controllers in your environment. In this post I'll go over what you need in order to install and use the Active Directory Module for PowerShell, also known as AD PowerShell.
Setting up your Domain Controllers
In order to use the Active Directory Module for Windows PowerShell on 2008 R2 and Windows 7, you first need to be running Active Directory Web Services (ADWS) on at least one Domain Controller. To install Active Directory Web Services (ADWS) you'll need one of the following:1. Windows Server 2008 R2 AD DS
You can load Active Directory Web Services (ADWS) on a Windows Server 2008 R2 Domain Controller when you install the AD DS role. The AD PowerShell module will also be installed during this process. Active Directory Web Services (ADWS) will be enabled when you promote the server to a DC using DCPromo.
2. Active Directory Management Gateway Service
If you cannot run Windows Server 2008 R2 Domain Controllers, you can install the Active Directory Management Gateway Service. Installing this will allow you to run the same Active Directory web service that runs on Windows Server 2008 R2 DC's. You can download the Active Directory Management Gateway Service here. Make sure you read the instructions carefully, there are several hotfixes that need to be applied depending on the version of Windows you are running. You can install the Active Directory Management Gateway Service on DC's running the following operating systems:
- Windows Server 2003 R2 with Service Pack 2
- Windows Server 2003 SP2
- Windows Server 2008
- Windows Server 2008 SP2
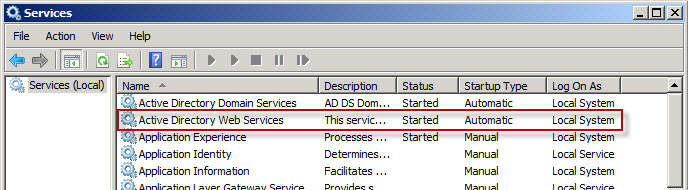
Once you've got Active Directory web services up and running on your Domain Controller(s), you'll notice you now have an ADWS service as shown here:
At this point, you should be ready to install the AD PowerShell module. You can run AD PowerShell on all versions of Windows Server 2008 R2 (except the Web Edition) and on Windows 7.
Installing the Active Directory Module for Windows PowerShell on 2008 R2 member servers
You can install the Active Directory Module on Windows 2008 R2 member servers by adding the RSAT-AD-PowerShell feature using the Server Manager. I usually use the ServerManager module to do this because it is quick and easy. To install the feature using the ServerManager module, launch PowerShell and run the following commands:Import-Module ServerManager
Add-WindowsFeature RSAT-AD-PowerShell
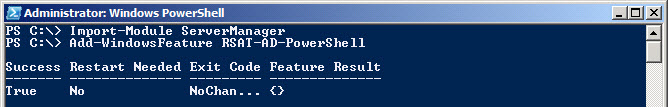
Remember, this only needs to be done on Windows Server 2008 R2 member servers. The RSAT-AD-PowerShell feature will be added to 2008 R2 DC's during the DCPromo process.
Installing the Remote Server Administration Tools (RSAT) feature on Windows 7
In order to install the Active Directory Module for Windows PowerShell you need to download the RSAT tools for Windows 7 here. Once this is installed you are still not finished, you need to enable the Active Directory module. Navigate to Control Panel > Programs and Features > Turn Windows Features On or Off and select Active Directory Module for Windows PowerShell as show here: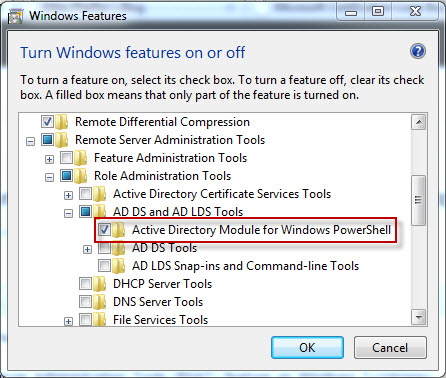
Once you have Active Directory web services running on at least one domain controller and the AD PowerShell module is installed, you are ready to run the AD PowerShell module. You can do this in one of two ways. First, you can access the "Active Directory Module for Windows PowerShell" shortcut in Administrative Tools as shown here:
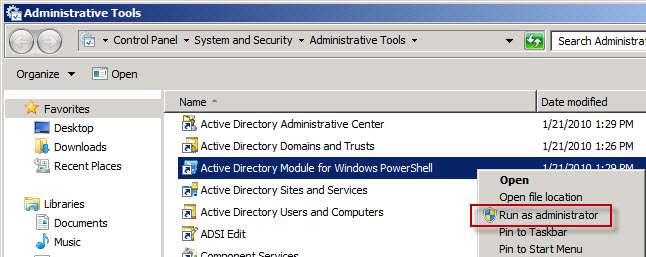
Right click the shortcut and select "Run as administrator" in order to start PowerShell with elevated permissions.
You can also simply import the AD PowerShell module in your existing PowerShell session. Just use the Import-Module ActiveDirectory command:
Import-Module ActiveDirectory
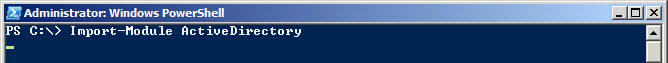
That's all that needs to be done to get up and running.
Below is a list of the new AD cmdlets that will be available and a synopsis of what they do.
| Name | Category | Synopsis |
| Add-ADComputerServiceAccount | Cmdlet | Adds one or more service accounts to an Active Directory computer. |
| Add-ADDomainControllerPasswordReplicationPolicy | Cmdlet | Adds users, computers, and groups to the allowed or denied list of a read-only domain controller password replication policy. |
| Add-ADFineGrainedPasswordPolicySubject | Cmdlet | Applies a fine-grained password policy to one more users and groups. |
| Add-ADGroupMember | Cmdlet | Adds one or more members to an Active Directory group. |
| Add-ADPrincipalGroupMembership | Cmdlet | Adds a member to one or more Active Directory groups. |
| Clear-ADAccountExpiration | Cmdlet | Clears the expiration date for an Active Directory account. |
| Disable-ADAccount | Cmdlet | Disables an Active Directory account. |
| Disable-ADOptionalFeature | Cmdlet | Disables an Active Directory optional feature. |
| Enable-ADAccount | Cmdlet | Enables an Active Directory account. |
| Enable-ADOptionalFeature | Cmdlet | Enables an Active Directory optional feature. |
| Get-ADAccountAuthorizationGroup | Cmdlet | Gets the accounts token group information. |
| Get-ADAccountResultantPasswordReplicationPolicy | Cmdlet | Gets the resultant password replication policy for an Active Directory account. |
| Get-ADComputer | Cmdlet | Gets one or more Active Directory computers. |
| Get-ADComputerServiceAccount | Cmdlet | Gets the service accounts hosted by a computer. |
| Get-ADDefaultDomainPasswordPolicy | Cmdlet | Gets the default password policy for an Active Directory domain. |
| Get-ADDomain | Cmdlet | Gets an Active Directory domain. |
| Get-ADDomainController | Cmdlet | Gets one or more Active Directory domain controllers based on discoverable services criteria, search parameters or by providing a domain controller identifier, such as the NetBIOS name. |
| Get-ADDomainControllerPasswordReplicationPolicy | Cmdlet | Gets the members of the allowed list or denied list of a read-only domain controller's password replication policy. |
| Get-ADDomainControllerPasswordReplicationPolicyUsage | Cmdlet | Gets the Active Directory accounts that are authenticated by a read-only domain controller or that are in the revealed list of the domain controller. |
| Get-ADFineGrainedPasswordPolicy | Cmdlet | Gets one or more Active Directory fine grained password policies. |
| Get-ADFineGrainedPasswordPolicySubject | Cmdlet | Gets the users and groups to which a fine grained password policy is applied. |
| Get-ADForest | Cmdlet | Gets an Active Directory forest. |
| Get-ADGroup | Cmdlet | Gets one or more Active Directory groups. |
| Get-ADGroupMember | Cmdlet | Gets the members of an Active Directory group. |
| Get-ADObject | Cmdlet | Gets one or more Active Directory objects. |
| Get-ADOptionalFeature | Cmdlet | Gets one or more Active Directory optional features. |
| Get-ADOrganizationalUnit | Cmdlet | Gets one or more Active Directory organizational units. |
| Get-ADPrincipalGroupMembership | Cmdlet | Gets the Active Directory groups that have a specified user, computer, group, or service account. |
| Get-ADRootDSE | Cmdlet | Gets the root of a Directory Server information tree. |
| Get-ADServiceAccount | Cmdlet | Gets one or more Active Directory service accounts. |
| Get-ADUser | Cmdlet | Gets one or more Active Directory users. |
| Get-ADUserResultantPasswordPolicy | Cmdlet | Gets the resultant password policy for a user. |
| Install-ADServiceAccount | Cmdlet | Installs an Active Directory service account on a computer. |
| Move-ADDirectoryServer | Cmdlet | Moves a directory server in Active Directory to a new site. |
| Move-ADDirectoryServerOperationMasterRole | Cmdlet | Moves operation master roles to an Active Directory directory server. |
| Move-ADObject | Cmdlet | Moves an Active Directory object or a container of objects to a different container or domain. |
| New-ADComputer | Cmdlet | Creates a new Active Directory computer. |
| New-ADFineGrainedPasswordPolicy | Cmdlet | Creates a new Active Directory fine grained password policy. |
| New-ADGroup | Cmdlet | Creates an Active Directory group. |
| New-ADObject | Cmdlet | Creates an Active Directory object. |
| New-ADOrganizationalUnit | Cmdlet | Creates a new Active Directory organizational unit. |
| New-ADServiceAccount | Cmdlet | Creates a new Active Directory service account. |
| New-ADUser | Cmdlet | Creates a new Active Directory user. |
| Remove-ADComputer | Cmdlet | Removes an Active Directory computer. |
| Remove-ADComputerServiceAccount | Cmdlet | Removes one or more service accounts from a computer. |
| Remove-ADDomainControllerPasswordReplicationPolicy | Cmdlet | Removes users, computers and groups from the allowed or denied list of a read-only domain controller password replication policy. |
| Remove-ADFineGrainedPasswordPolicy | Cmdlet | Removes an Active Directory fine grained password policy. |
| Remove-ADFineGrainedPasswordPolicySubject | Cmdlet | Removes one or more users from a fine grained password policy. |
| Remove-ADGroup | Cmdlet | Removes an Active Directory group. |
| Remove-ADGroupMember | Cmdlet | Removes one or more members from an Active Directory group. |
| Remove-ADObject | Cmdlet | Removes an Active Directory object. |
| Remove-ADOrganizationalUnit | Cmdlet | Removes an Active Directory organizational unit. |
| Remove-ADPrincipalGroupMembership | Cmdlet | Removes a member from one or more Active Directory groups. |
| Remove-ADServiceAccount | Cmdlet | Remove an Active Directory service account. |
| Remove-ADUser | Cmdlet | Removes an Active Directory user. |
| Rename-ADObject | Cmdlet | Changes the name of an Active Directory object. |
| Reset-ADServiceAccountPassword | Cmdlet | Resets the service account password for a computer. |
| Restore-ADObject | Cmdlet | Restores an Active Directory object. |
| Search-ADAccount | Cmdlet | Gets Active Directory user, computer, or service accounts. |
| Set-ADAccountControl | Cmdlet | Modifies user account control (UAC) values for an Active Directory account. |
| Set-ADAccountExpiration | Cmdlet | Sets the expiration date for an Active Directory account. |
| Set-ADAccountPassword | Cmdlet | Modifies the password of an Active Directory account. |
| Set-ADComputer | Cmdlet | Modifies an Active Directory computer object. |
| Set-ADDefaultDomainPasswordPolicy | Cmdlet | Modifies the default password policy for an Active Directory domain. |
| Set-ADDomain | Cmdlet | Modifies an Active Directory domain. |
| Set-ADDomainMode | Cmdlet | Sets the domain mode for an Active Directory domain. |
| Set-ADFineGrainedPasswordPolicy | Cmdlet | Modifies an Active Directory fine grained password policy. |
| Set-ADForest | Cmdlet | Modifies an Active Directory forest. |
| Set-ADForestMode | Cmdlet | Sets the forest mode for an Active Directory forest. |
| Set-ADGroup | Cmdlet | Modifies an Active Directory group. |
| Set-ADObject | Cmdlet | Modifies an Active Directory object. |
| Set-ADOrganizationalUnit | Cmdlet | Modifies an Active Directory organizational unit. |
| Set-ADServiceAccount | Cmdlet | Modifies an Active Directory service account. |
| Set-ADUser | Cmdlet | Modifies an Active Directory user. |
| Uninstall-ADServiceAccount | Cmdlet | Uninstalls an Active Directory service account from a computer. |